Home /
Expert Answers /
Computer Science /
we-should-probably-start-with-a-standard-cybersecurity-model-to-best-guide-our-policies-on-informati-pa691
(Solved): We should probably start with a standard cybersecurity model to best guide our policies on informati ...
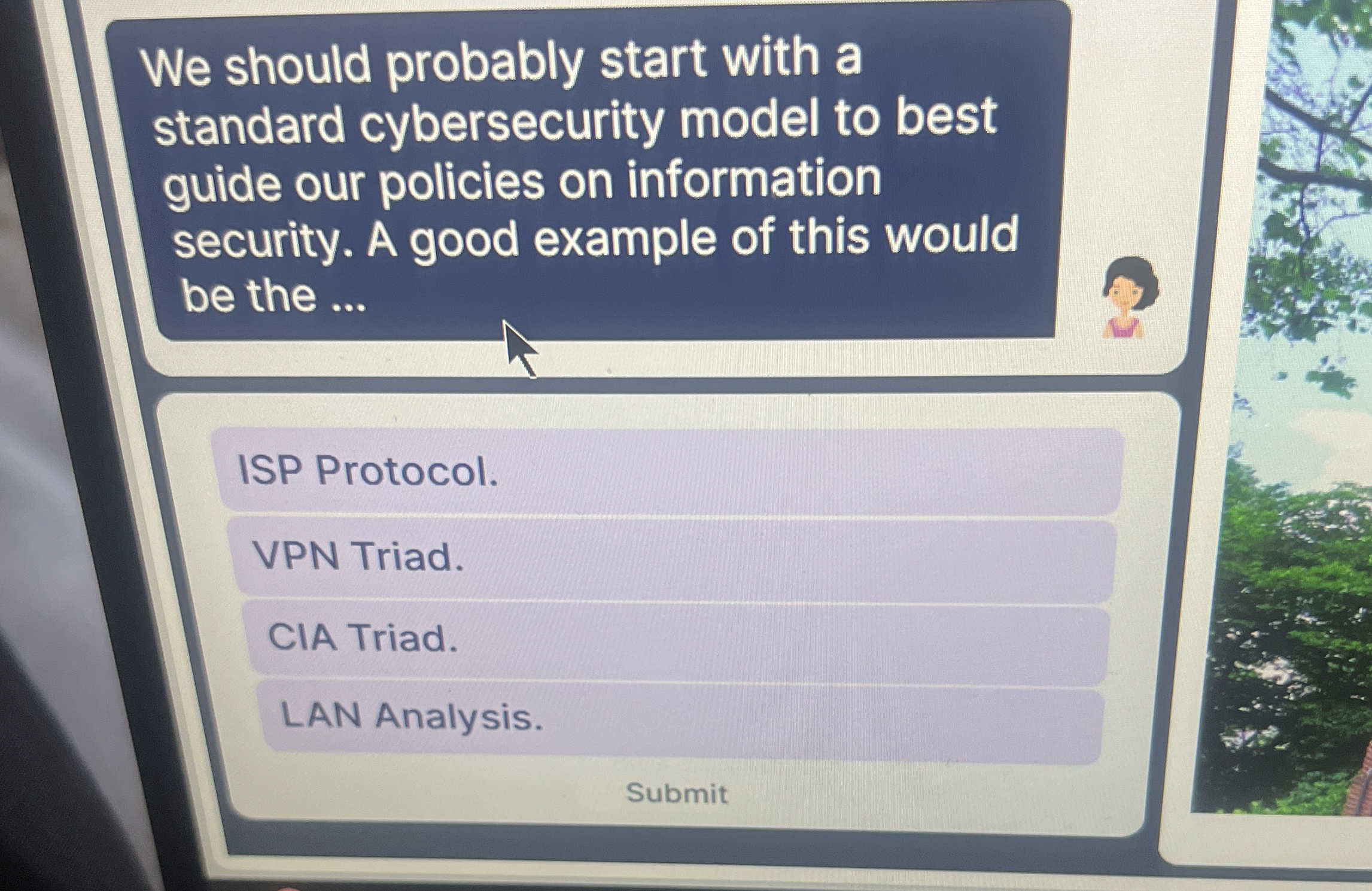
We should probably start with a standard cybersecurity model to best guide our policies on information security. A good example of this would be the ... ISP Protocol. VPN Triad. CIA Triad. LAN Analysis. SubmitWe should probably start with a standard cybersecurity model to best guide our policies on information security. A good example of this would be the ... ISP Protocol. VPN Triad. CIA Triad. LAN Analysis. Submit